Pentesting on the Fly : Android Phone - Prelude : Setting Up the Environment
Hey there !
Seems like the idea of this series was interesting to some people. That's why I post now the prelude : Setting up the environment
This article comes from my previous post :
http://null-byte.wonderhowto.com/forum/kali-linux-android-phone-with-metasploit-aircrack-ng-john-tmux-0160861/
It was re-arranged to be designed with our new goals.
Please notice that we only use Open-Source Tools so it has nothing in common with zanti or Dsploit
II) Downloads :
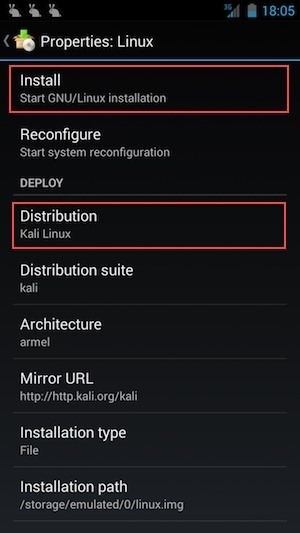
Dowload Linux Deploy from the app store
Download an SSH client or TerminalIDE
III) Setting up the Download:
- Launch Linux Deploy
We only want a tiny image, with specific Tools. This is surgical strike minded so :
-> Tap on "Image size (MB)" and enter the amount of memory you want to allocate. I suggest 2200 MB (2,2GB)
-> Then, go to "Compents to install, and UNCHECK EVERYTHING EXCEPT SSH SERVER.
This will have the image you download much more tiny, so you'll have more free space to install our Tools
V) Make your internal storage accessible from within the image
You have to consider the fact that you're running a chrooted environment.
So, in order to access to the internal sotrage, yo have to go into Linux Deploy options :
-> Scroll down to "Custom Mounts" and enable it. Then tap on "Mount points" and enable one of the presented path.
-> Choose the one corresponding to your storage, for example, on my phone it was : /storage/emulated/0
It will allow you, once you've booted your linux img to access your internal storage in the /mnt/ directory ( for example on my phone : /mnt/0)
VI) Boot your image :
Tap "Launch"
VII) Connect to your Hacking Environment :
1) Using TerminalIDE (or any command line ssh) :
ssh android@localhost
type in the following password : 'changeme' (without quotes)
2) Using an ssh client (instable)
Follow the onscreen instruction to set up the client to connect to localhost on port 22 with "android" as name
VIII) Update it :
Type :
apt-get update && apt-get dist-upgrade
______________
DONE !
Your environment is set up and ready to run.
In the nexts post we'll set up specifics attacks, and specifics Tools :)
See ya !
Also feel free to post suggestions :)

Aucun commentaire:
Enregistrer un commentaire