Pentesting on the Fly : Android Phone - Part 3) My Phone Is a Recon Machine
Let's take it a step further and go back to hacking's first step : RECON--Keep in Mind that at each chapter you'll need to launch Linux Deploy, tap "Start", and then SSH android@localhost and type in changeme --
0) SCENARIO
I took plane a few hours ago to get back home and I landed at Chicago's airport for a short stopover. I have around two hours before taking off one again.
Guess what ? I'm sitting on chair and i'm bored...
I'd like to pentest them, but first I need to scan their systems and... I'd rather not use Tor, too slow... So I need a new IP not related to me.
There must be one of thoses pre-paid SIM cards including mobiles data ! I enter the shop and get one (for 20 bucks...):
FIRE ! I GRAB MY PHONE!!!
Today we'll start a recon on our target systems :
Two basics Tools :
- Nmap
- Any vulnerability scanner compatible with command line only and sufficiently light
- Optional :DNS discovery tool (won't be treated here, we keep it light and efficient.
- Have sucessfully set up the environment following this tutorial
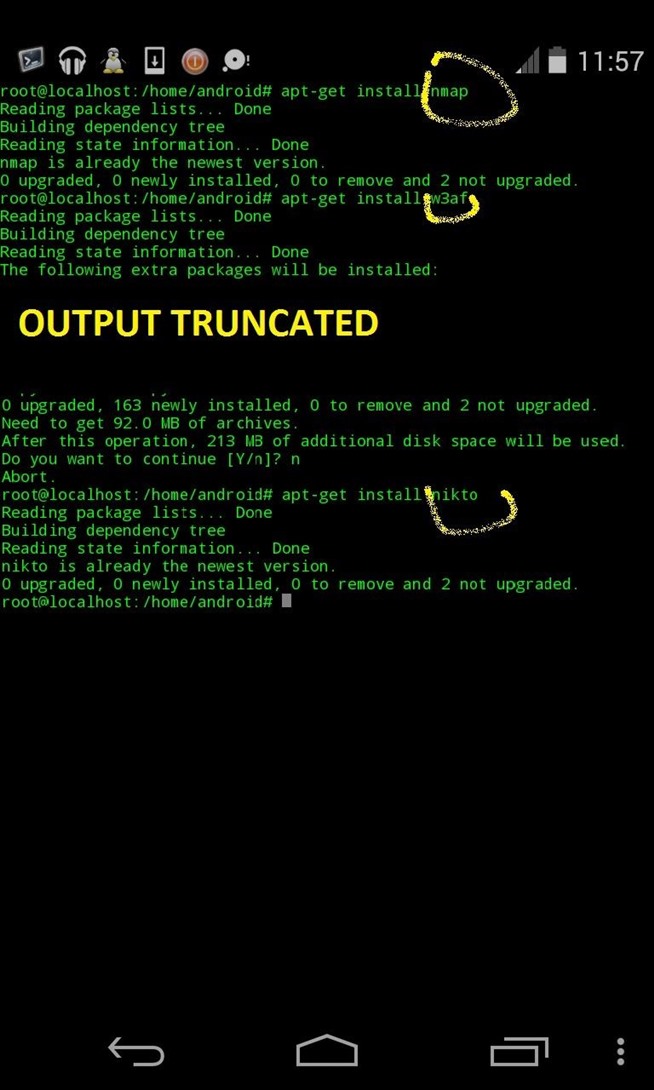
- Nmap installed
- W3af installed
- Nikto installed
Nmap :
apt-get install nmap
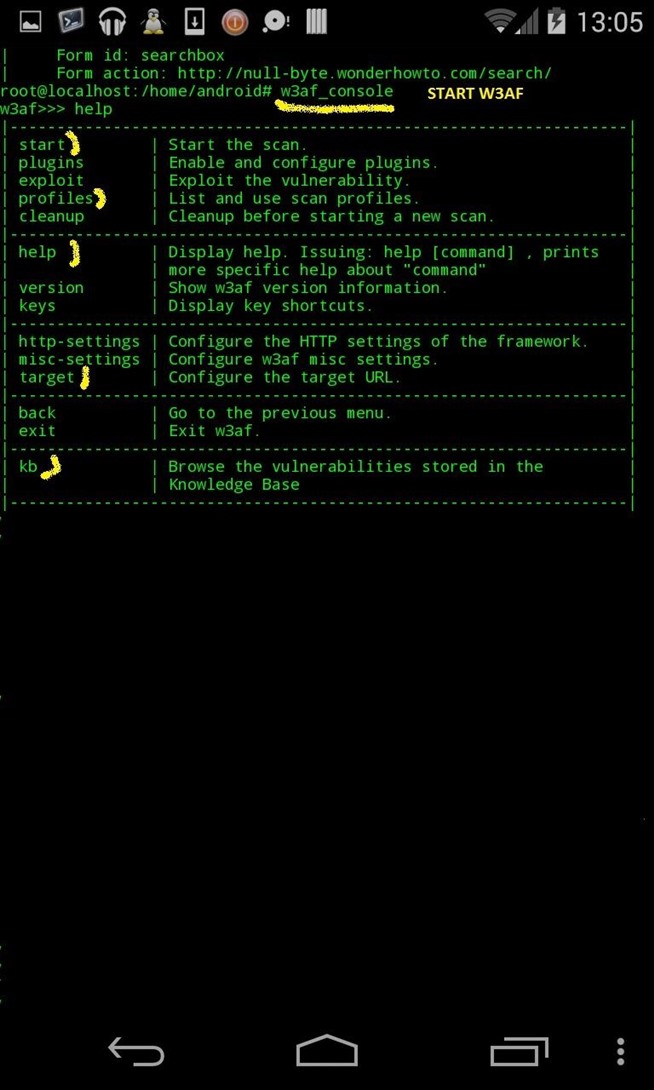
W3af:
apt-get install w3af
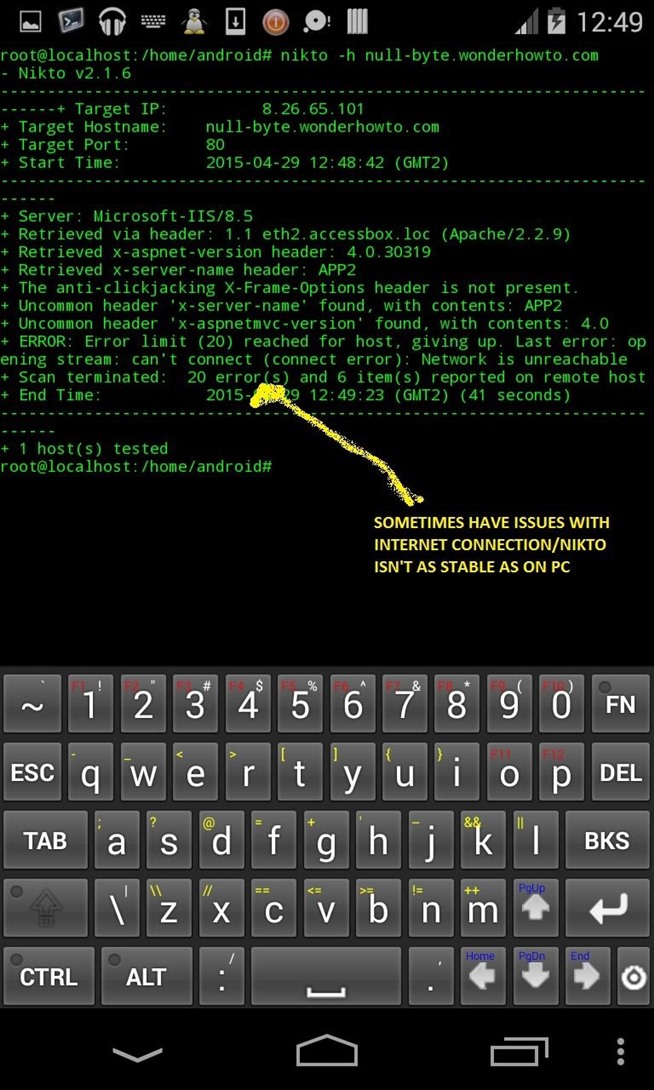
Nikto:
apt-get install nikto
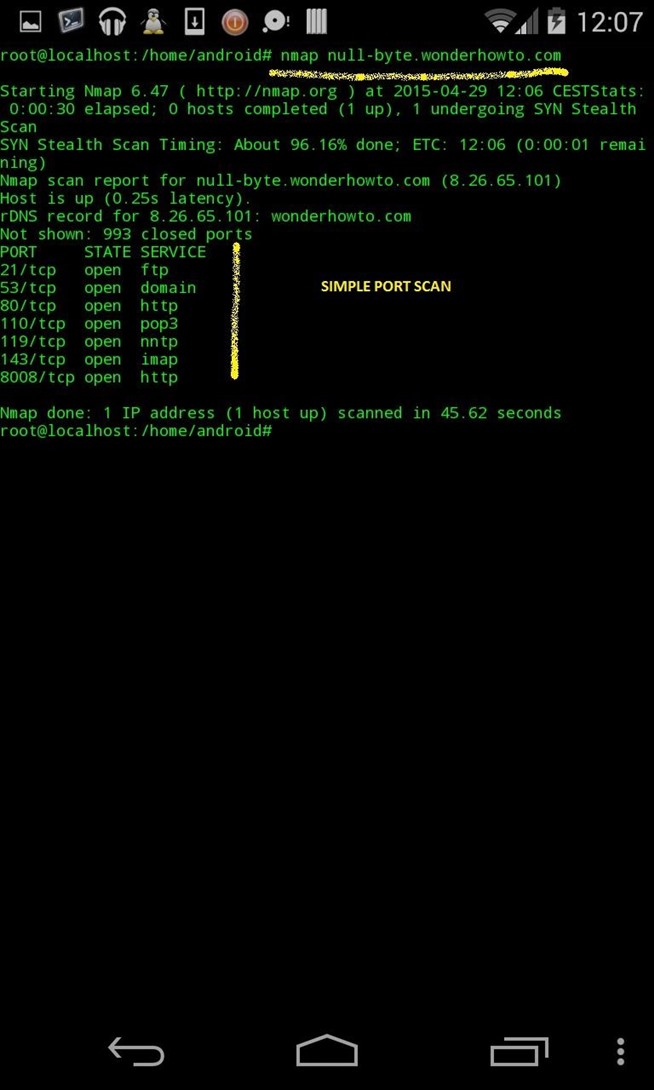
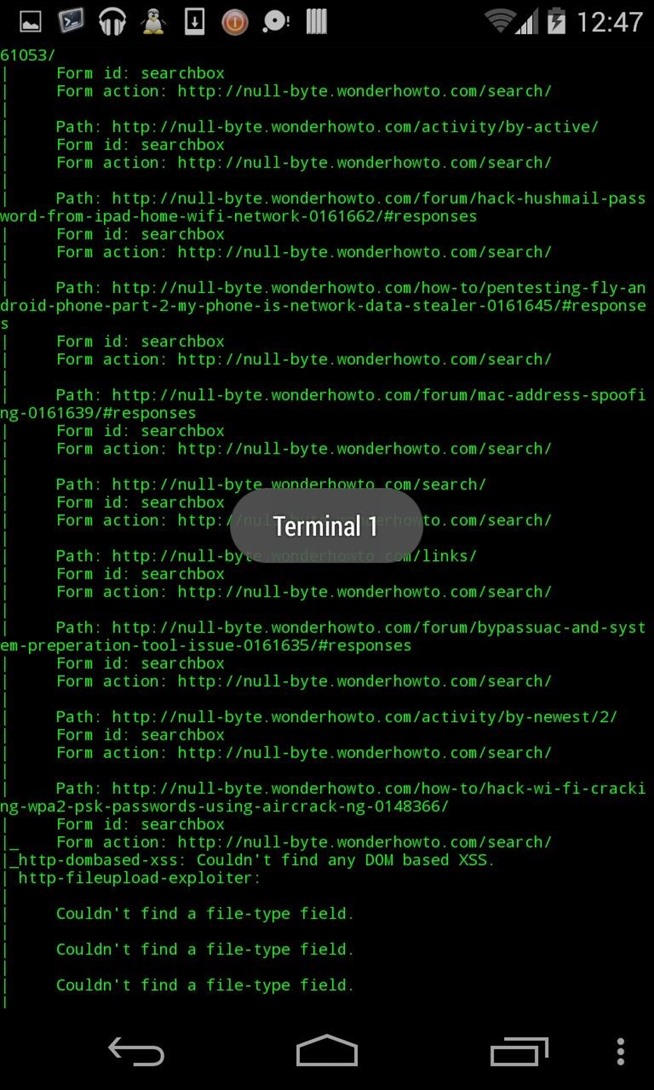
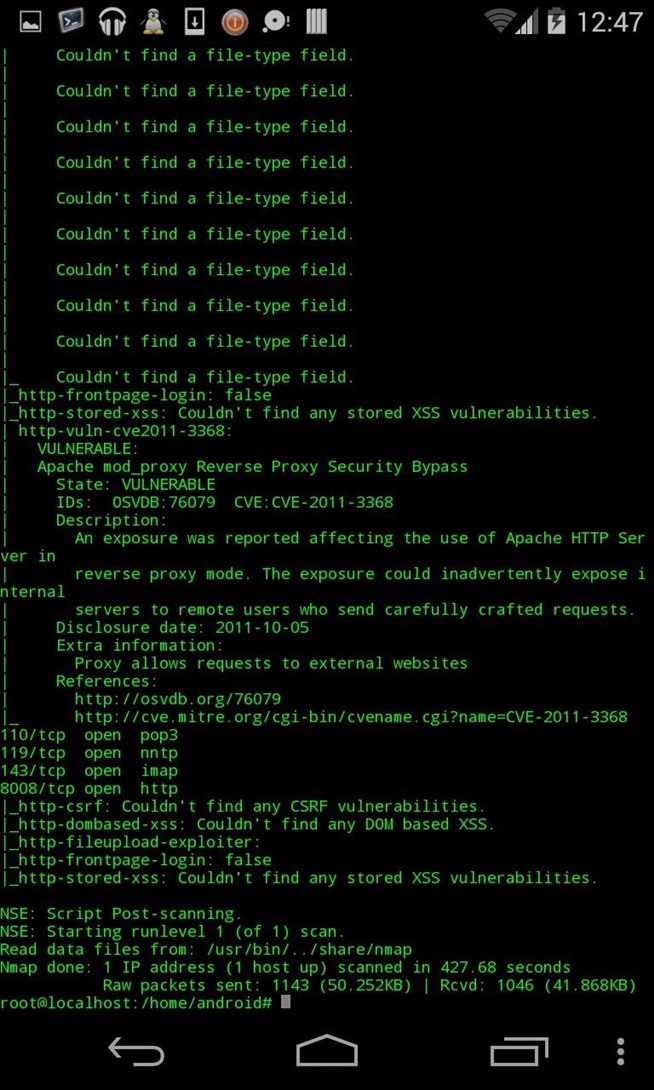
(basic scan without options) :
nmap null-byte.wonderhowto.com
nikto -h "null-byte.wonderhowto.com
w3af_console
There's full of possibilites with W3AF, i give you two links to learn how to master its possibilities with command line :
http://pentesterconfessions.blogspot.fr/2007/10/how-to-use-w3af-to-audit-web.html
http://resources.infosecinstitute.com/w3af-tutorial/
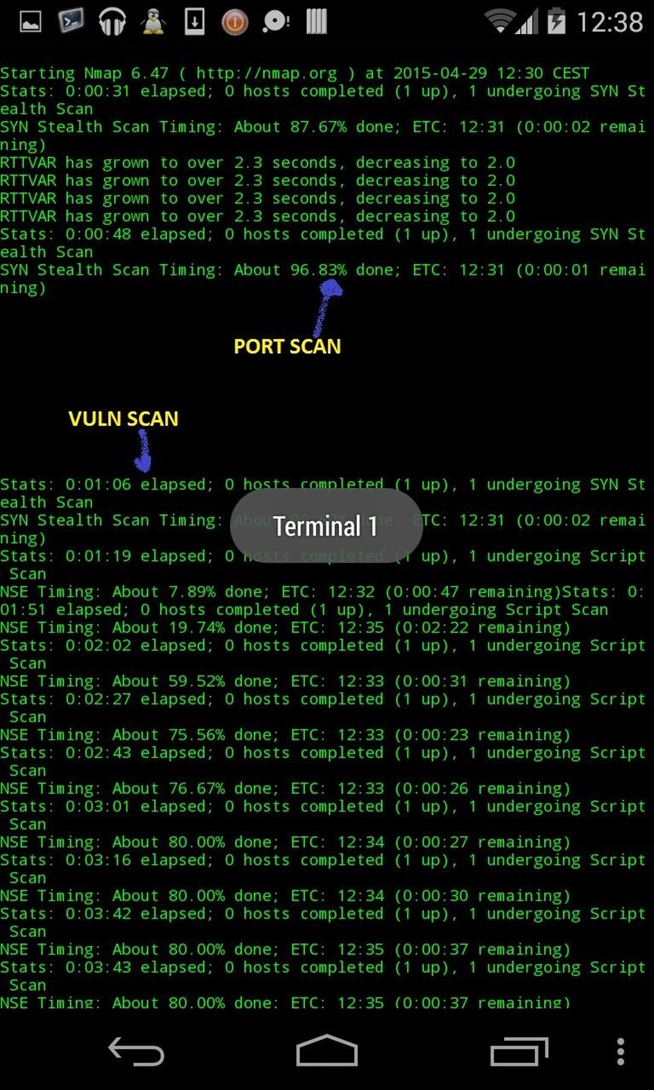
Let's set up scan :
1) see options : help
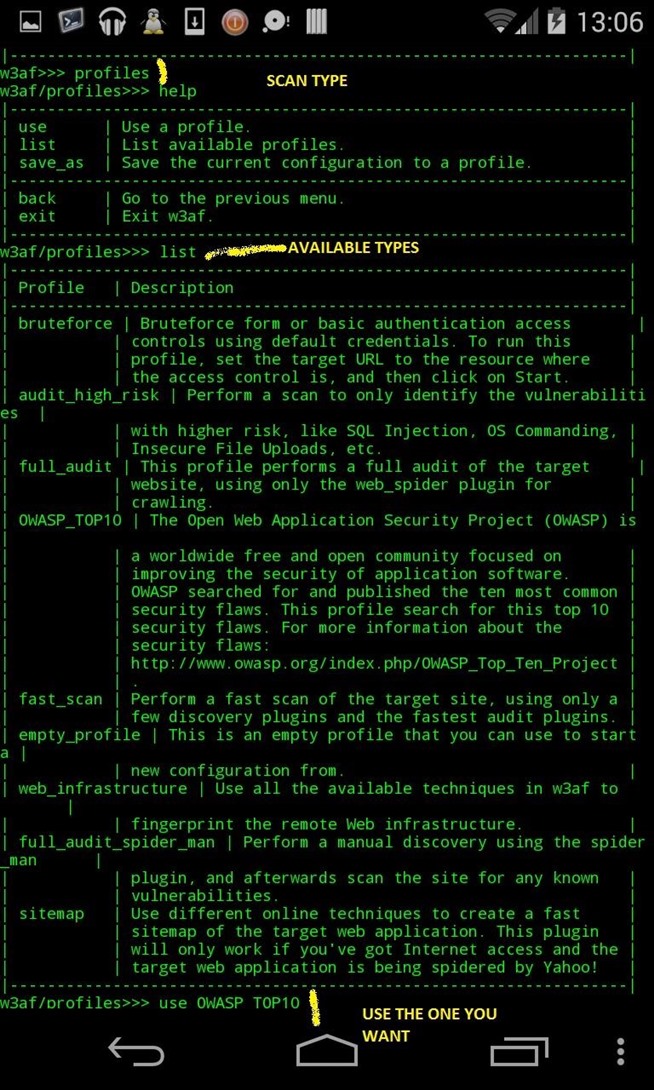
2) Set up FIRST the profile (type of scan, there's a lot, here we'll use OWASP_TOP10)
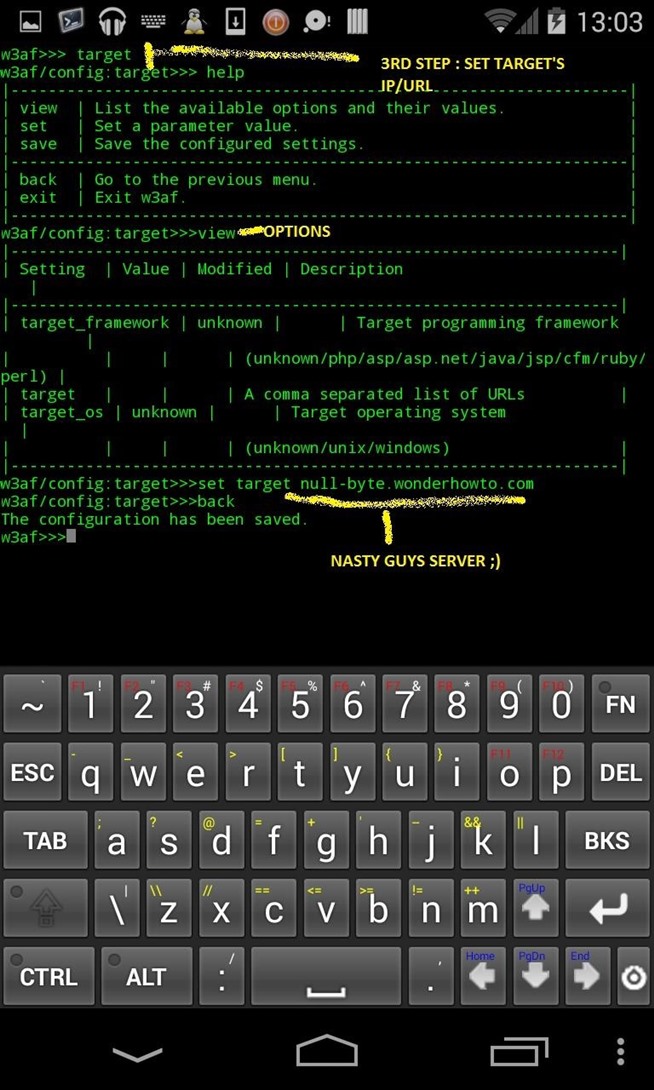
3) THEN set up target
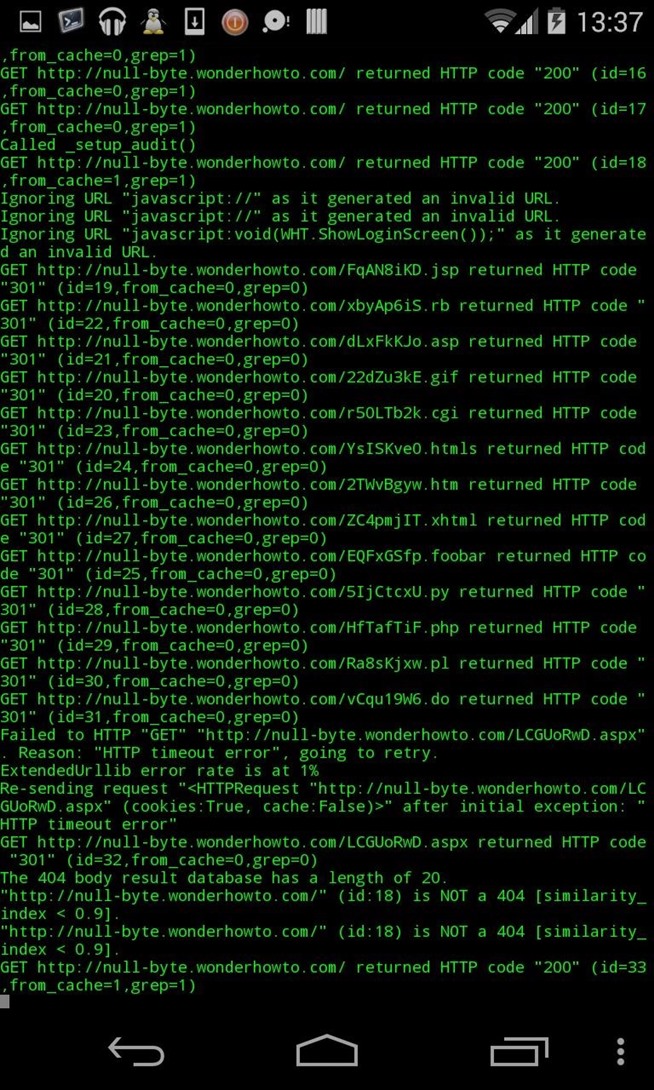
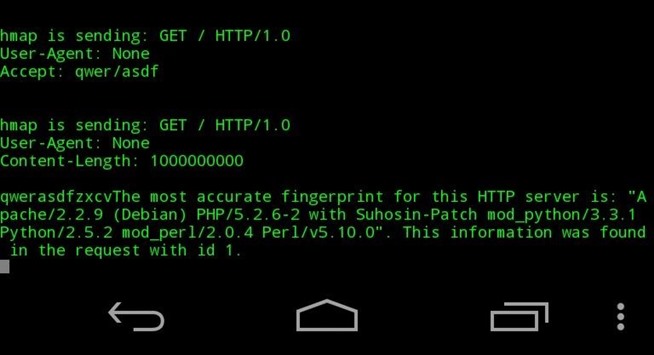
4) Scan
5) List vulns/shells/exploits
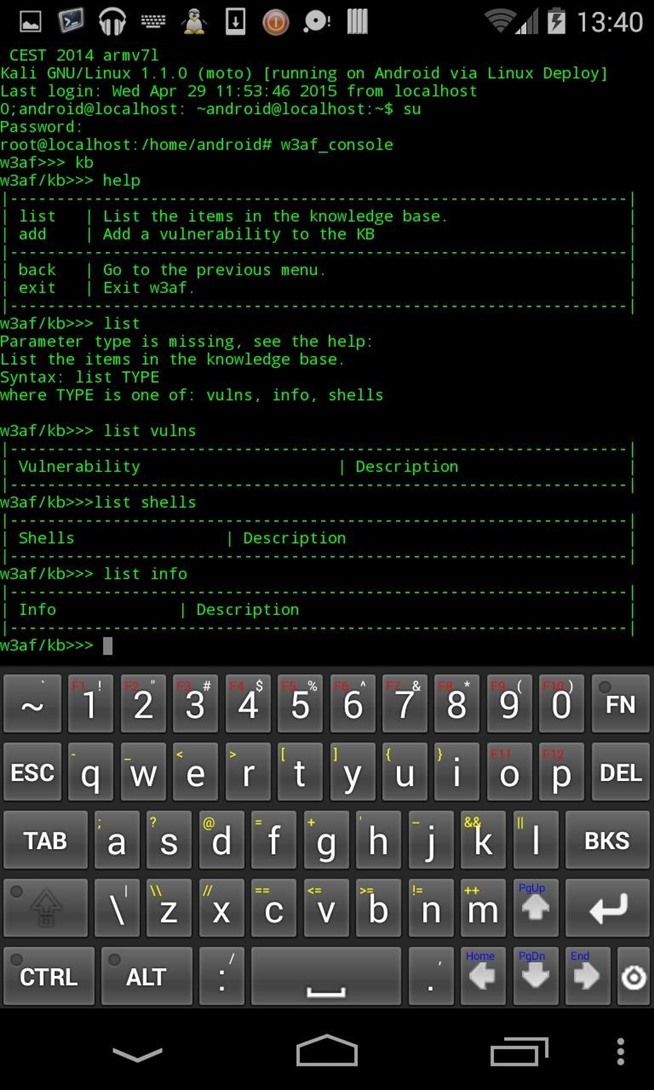
help
use profile OWASP_TOP10
help
set target null-byte.wonderhowto.com
back
- Scan done
- Ip range scanned
- Ports scanned
- Quick vuln scan made with 2 différents tools
- IP hidden by using a prepaid sim, paid with cash
- Traceable, but can't be related to anything, except a hack launched in an airport where thousands of people transit in one day
- No obvious traces on CCTV : Phone left in Pocket during the whole scan (except for typing some lines, but looks like texting)
- But i'd strongly suggest you don't use the card just after you paid it -too obvious-, buy one and use days later
Great ! I performed the scan stealthly and quickly, and I can move almost immediatly so I won't be traced.
I remove the prepaid SIM, go to the nearest WC, locate a cleaning trolley, steal some bleach, spread it on the sim card, grind it Under my feet, then I go out of the airport and discreetly launch the rest of it into a taxi car boot.
I now know that their servers are located in Japan, and that they hide infos about a kind of secret organization conspiring for internet's total Control.
The IP is located in Okinawa at Naha city?
Now I know where I go. I exchange my tickets and fly to Kyoto. This time i'll get into their systems once for all and know where all this leads.
Even if I have to enter their offices.
Post Scriptum :
I got authorization to perform the scan from Bryan Crow, followed by Justin Meyers and Occupytheweb (all three administrators and moderators)
Pentesting a non-consenting target is illegal, so please don't fire up your phones and vuln
_______________






Aucun commentaire:
Enregistrer un commentaire